Network traffic analyzer sniffer. What is a sniffer: description. Sniffer - what kind of beast Download the sniffer program in Russian
In this article, we will look at creating a simple sniffer for Windows OS.
Who cares, welcome under cat.
Introduction
Target: write a program that will capture network traffic (Ethernet, WiFi) transmitted over the IP protocol.Facilities:visual studio 2005 or higher.
The approach described here does not belong personally to the author and has been successfully applied in many commercial, as well as categorically free programs(hello, GPL).
This work is intended primarily for beginners in network programming, who, however, have at least basic knowledge of sockets in general, and windows sockets in particular. Here I will often write well-known things, because the subject area is specific, if you miss something, there will be mess in your head.
I hope you find it interesting.
Theory (reading is optional, but desirable)
At present, the vast majority of modern information networks are based on the foundation of the TCP/IP protocol stack. The TCP/IP (Transmission Control Protocol/Internet Protocol) protocol stack is a collective name for network protocols of different levels used in networks. In this article, we will be mainly interested in the IP protocol - routable network protocol, used for non-guaranteed delivery of data, divided into so-called packets (a more correct term is datagram) from one network node to another.Of particular interest to us are IP packets intended for the transmission of information. This is a sufficiently high level of the OSI network data model, when it is possible to abstract from the device and the data transmission medium, operating only with a logical representation.
It is quite logical that sooner or later tools for interception, control, accounting and analysis of network traffic should appear. Such tools are usually called traffic analyzers, packet analyzers or sniffers (from English to sniff - sniff). This is a network traffic analyzer, a program or software and hardware device designed to intercept and then analyze, or only analyze network traffic destined for other nodes.
Practice (talk to the point)
At the moment, quite a lot has been created software to listen to traffic. The most famous of them: Wireshark. Naturally, the goal is not worth reaping his laurels - we are interested in the task of intercepting traffic by the usual "listening" of the network interface. It is important to understand that we are not going to engage in hacking and intercepting stranger traffic. You just need to view and analyze the traffic that passes through our host.Why it might be needed:
- View the current traffic flow through the network connection (incoming/outgoing/total).
- Redirect traffic for further analysis to another host.
- Theoretically, you can try to use it to hack a WiFi network (we're not going to do this, right?).
How so? Very simple.
The key step in turning a simple network application into a network analyzer is to switch the network interface to promiscuous mode, which will allow it to receive packets addressed to other interfaces on the network. This mode forces the network card to accept all frames, regardless of who they are addressed to on the network.
Starting with Windows 2000 (NT 5.0), creating a program to listen on a network segment has become very easy, because her network driver allows you to put the socket in the mode of receiving all packets.
Enabling promiscuous mode
long flag = 1; SOCKET socket; #define SIO_RCVALL 0x98000001 ioctlsocket(socket, SIO_RCVALL, &RS_Flag);Our program operates on IP packets and uses the Windows Sockets library version 2.2 and raw sockets. In order to directly access an IP packet, the socket must be created as follows:
Creating a Raw Socket
s = socket(AF_INET, SOCK_RAW, IPPROTO_IP);Here instead of a constant SOCK_STREAM(TCP protocol) or SOCK_DGRAM(UDP protocol), we use the value SOCK_RAW. Generally speaking, working with raw sockets is interesting not only from the point of view of capturing traffic. In fact, we get full control over the formation of the package. Or rather, we form it manually, which allows, for example, to send a specific ICMP packet ...
Go ahead. It is known that an IP packet consists of a header, service information and, in fact, data. I advise you to look here to refresh your knowledge. Let's describe the IP header as a structure (thanks to the excellent article on RSDN):
Description of the structure of the IP packet
typedef struct _IPHeader ( unsigned char ver_len; // header version and length unsigned char tos; // service type unsigned short length; // length of the entire packet unsigned short id; // Id unsigned short flgs_offset; // flags and offset unsigned char ttl ; // lifetime unsigned char protocol; // protocol unsigned short xsum; // checksum unsigned long src; // source IP address unsigned long dest; // destination IP address unsigned short *params; // parameters (up to 320 bits) unsigned char *data; // data (up to 65535 octets) )IPHeader;The main function of the listening algorithm will look like this:
Single Packet Capture Function
IPHeader* RS_Sniff() ( IPHeader *hdr; int count = 0; count = recv(RS_SSocket, (char*)&RS_Buffer, sizeof(RS_Buffer), 0); if (count >= sizeof(IPHeader)) ( hdr = (LPIPHeader )malloc(MAX_PACKET_SIZE); memcpy(hdr, RS_Buffer, MAX_PACKET_SIZE); RS_UpdateNetStat(count, hdr); return hdr; ) else return 0; )Everything is simple here: we get a portion of data using the standard socket function recv, and then copy them into a structure like IPHeader.
And finally, we start an infinite packet capture loop:
Capturing all packets that will hit our network interface
while (true) ( IPHeader* hdr = RS_Sniff(); // process IP packet if (hdr) ( // print header in console ) )A little offtopic
Hereinafter, the author prefixed some important functions and variables with RS_ (from Raw Sockets). The project was done 3-4 years ago, and there was a crazy idea to write a full-fledged library for working with raw sockets. As is often the case, after obtaining any significant (for the author) results, the enthusiasm faded, and the matter did not go further than the training example.In principle, you can go further and describe the headers of all subsequent protocols above. To do this, it is necessary to analyze the field protocol in structure IPHeader. Look at the code example (yes, there should be a switch, damn it!), where the header is colored depending on which protocol the IP-encapsulated packet has:
/* * Packet highlighting */ void ColorPacket(const IPHeader *h, const u_long haddr, const u_long whost = 0) ( if (h->xsum) SetConsoleTextColor(0x17); // if the pack is not empty else SetConsoleTextColor(0x07) ; // empty package if (haddr == h->src) ( SetConsoleTextColor(BACKGROUND_BLUE | /*BACKGROUND_INTENSITY |*/ FOREGROUND_RED | FOREGROUND_INTENSITY); // "native" return package ) else if (haddr == h->dest ) ( SetConsoleTextColor(BACKGROUND_BLUE | /*BACKGROUND_INTENSITY |*/ FOREGROUND_GREEN | FOREGROUND_INTENSITY); // "native" receive packet ) if (h->protocol == PROT_ICMP || h->protocol == PROT_IGMP) ( SetConsoleTextColor(0x70) ; // ICMP packet ) else if(h->protocol == PROT_IP || h->protocol == 115) ( SetConsoleTextColor(0x4F); // IP-in-IP packet, L2TP ) else if(h- >protocol == 53 || h->protocol == 56) ( SetConsoleTextColor(0x4C); // TLS, IP with Encryption ) if(whost == h->dest || whost == h->src) ( SetConsoleTextColor (0x0A); ) )
However, this is substantially beyond the scope of this article. For our training example, it will be enough to look at the ip-addresses of the hosts from which and to which the traffic goes, and calculate its amount per unit of time (the finished program is in the archive at the end of the article).
In order to display IP header data, a function must be implemented to convert the datagram header (but not the data) to a string. As an example implementation, we can offer the following option:
Converting an IP Header to a String
inline char* iph2str(IPHeader *iph) ( const int BUF_SIZE = 1024; char *r = (char*)malloc(BUF_SIZE); memset((void*)r, 0, BUF_SIZE); sprintf(r, "ver=% d hlen=%d tos=%d len=%d id=%d flags=0x%X offset=%d ttl=%dms prot=%d crc=0x%X src=%s dest=%s", BYTE_H (iph->ver_len), BYTE_L(iph->ver_len)*4, iph->tos, ntohs(iph->length), ntohs(iph->id), IP_FLAGS(ntohs(iph->flgs_offset)), IP_OFFSET (ntohs(iph->flgs_offset)), iph->ttl, iph->protocol, ntohs(iph->xsum), nethost2str(iph->src), nethost2str(iph->dest)); return r; )Based on the above basic information, we get such a small program (the terrible name ss, short for English simple sniffer), which implements local listening to IP traffic. Its interface is shown below in the figure.
I provide the source and binary code as is, as it was several years ago. Now I'm scared to look at it, and yet, it is quite readable (of course, you can't be so self-confident). Even Visual Studio Express 2005 will suffice for compilation.
What we ended up with:
- The sniffer runs in user mode, but requires administrator privileges.
- Packets are not filtered, displaying as is (custom filters can be added - I suggest we cover this topic in detail in the next article, if interested).
- WiFi traffic is also captured (it all depends on the specific chip model, it may not work for you, as it did for me a few years ago), although there is AirPcap, which can do this wonderfully, but costs money.
- The entire datagram stream is logged to a file (see the archive attached at the end of the article).
- The program runs as a server on port 2000. You can telnet to a host and monitor traffic flows. The number of connections is limited to twenty (the code is not mine, I found it on the Internet and used it for experiments; I didn’t delete it - it’s a pity)
When an ordinary user hears the term "sniffer", he immediately becomes interested in what it is and why it is needed.
We will try to explain everything in simple terms.
However, this article will be intended not only for novice users, but also for.
Definition
Sniffer is a traffic analyzer. In turn, traffic is all the information that passes through computer networks.
This analyzer looks at what information is being transmitted. To do this, it must be intercepted. In fact, this is an illegal thing, because in this way people often get access to other people's data.
It can be compared to a train robbery - the classic plot of most westerns.
You are transferring some information to another user. She is driven by a "train", that is, a network channel.
Assholes from the gang of bloody Joe intercept the train and rob it to the skin. In our case, the information goes further, that is, attackers do not steal it in the truest sense of the word.
But let's say that this information is passwords, personal records, photos and the like.
Attackers can simply rewrite and photograph it all. In this way, they will have access to sensitive data that you would like to hide.
Yes, you will have all this information, it will reach you.
But you will know that complete strangers know the same thing. But in the 21st century, information is most valued!
In our case, this principle is used. Certain people stop traffic, read data from it and send it further.
True, in the case of sniffers, everything is not always so scary. They are used not only to gain unauthorized access to data, but also to analyze the traffic itself. This is an important part of the work of system administrators and just administrators of various resources. It is worth talking about the application in more detail. But before that, we will touch on how these same sniffers work.
Principle of operation
In practice, sniffers can be portable devices that are literally placed on a cable and read data and programs from it.
In some cases, this is simply a set of instructions, that is, codes that must be entered in a certain sequence and in a certain programming environment.
If in more detail that the interception of traffic by such devices can be read in one of the following ways:
1 By installing hubs instead of switches. In principle, listening to a network interface can be done in other ways, but they are all ineffective.
2 By connecting a literal sniffer to the channel break. This is exactly what was discussed above - and is put small device, which reads everything that moves along the channel.
3 Installing a branch from traffic. This branch is routed to some other device, possibly decrypted, and sent to the user.
4 An attack aimed at completely redirecting traffic to a sniffer. Of course, after the information enters the reader, it is again sent to the end user, to whom it was originally intended. in its purest form!
5 By analyzing electromagnetic radiation that arise due to the movement of traffic. This is the most complex and rarely used method.
Here is an example of how the second method works.
True, here it is shown that the reader is simply connected to the cable.
In fact, doing it this way is almost impossible.
The fact is that the end user will still notice that in some place there is a break in the channel.

The very principle of operation of a conventional sniffer is based on the fact that within one segment they are sent to all connected machines. Silly enough, but so far there is no alternative method! And between the segments, data is transmitted using switches. This is where the possibility of intercepting information by one of the above methods appears.
Actually, this is called cyber attacks and hacking!
By the way, if you correctly install these same switches, you can completely protect the segment from all kinds of cyber attacks.
There are other methods of protection, which we will talk about at the very end.
Helpful information:
Pay attention to the program. It is used to analyze network traffic and parse data packets, for which the pcap library is used. This significantly narrows the number of packages available for parsing, since only those packages that are supported by this library can be parsed.
Application
Of course, first of all, this concept has the application discussed above, that is, hacker attacks and illegal obtaining of user data.
But besides this, sniffers are also used in other areas, and specifically, in work. system administrators.
In particular, such devices The programs help you to do the following:

As you can see, the devices or programs we are considering can greatly facilitate the work of system administrators and other people who use networks. And that's all of us.
Now let's move on to the most interesting - an overview of sniffer programs.
We figured out above that they can be made in the form of physical devices, but in most cases special ones are used.
Let's study them.
Sniffer programs
Here is a list of the most popular such programs:
commview. The program is paid, like all the others on our list. One minimum license costs $300. But the functionality of the software is richest. The first thing worth noting is the possibility of self-setting rules. For example, you can make it so that (these protocols) are completely ignored. It is also noteworthy that the program allows you to view the details and log of all forwarded packets. There is a regular version and a Wi-Fi version.

Spynet. This is, in fact, the Trojan that we are all so tired of. But it can also be used for the noble purposes we talked about above. The program intercepts and that are in the traffic. There are many unusual features. For example, you can recreate the pages on the Internet that the "victim" visited. It is noteworthy that this software is free, but it is quite difficult to find it.

BUTTSniffer. This is a sniffer in its purest form, which helps to analyze network packets, and not to intercept other people's passwords and browser history. At least that's what the author thought. In fact, his creation is used, you know what. This is a regular batch program that works through command line. To get started, two files are downloaded and run. The "captured" packets are stored on the hard disk, which is very convenient.
There are many other sniffer programs out there. For example, fsniff, WinDump, dsniff, NatasX, NetXRay, CooperSniffer, LanExplorer, Net Analyzer and many others are known. Choose any! But, in fairness, it should be noted that the best is CommView.
So, we have analyzed what sniffers are, how they work and what they are.
Now let's move from the place of a hacker or system administrator to the place of an ordinary user.
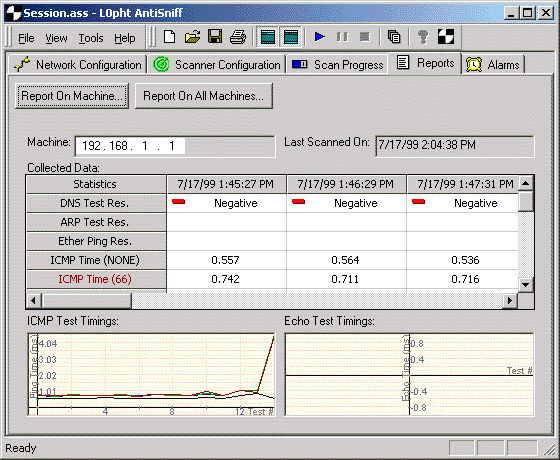
We are well aware that our data can be stolen. What to do to prevent this from happening? (here). It works extremely simply - it scans the network for all kinds of spies and reports if any are found. This is the simplest and most understandable principle that allows you to protect yourself from cyber attacks.
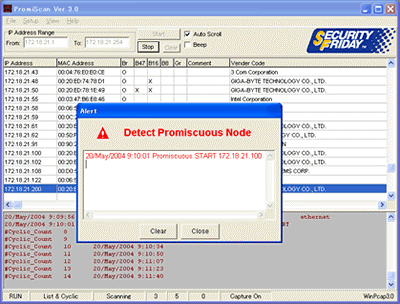
3 Use PromScan. In terms of its properties and tasks, this program is very similar to AntiSniff for Windows so pick one. There are also many download links on the net (here is one of them). This is an innovative program that allows you to remotely control computers connected to the same network. The principle of its operation is to determine the nodes that should not be in the network. Actually, this, most likely, is the sniffers. The program detects them and signals this with an eloquent message. Very comfortably!.
4 Use cryptography, and if deployed, a public key cryptographic system. This is a special encryption system or electronic signature. Its “trick” is that the key is public and everyone can see it, but it is impossible to change the data, since this must be done on all computers on the network at the same time. A wonderful method is like bait for a thief. In you can read about the blockchain, where such a system is used.
5 Do not download suspicious programs, do not go to suspicious sites, and so on. Every modern user knows about this, and yet it is this path that is the main one for Trojans and other dirty tricks to get into your computer. operating system. Therefore, be very responsible when using the Internet in principle!
If you have any more questions, ask them in the comments below.
We hope we were able to explain everything in a simple and understandable language.
Each of the ][ team has their own preferences regarding software and utilities for
pen test. After consulting, we found out that the choice varies so much that you can
make a real gentleman's set of proven programs. On that and
decided. In order not to make a combined hodgepodge, we divided the entire list into topics - and in
this time we'll touch on utilities for sniffing and packet manipulation. Use on
health.
Wireshark
netcat
If we talk about data interception, then network miner take it off the air
(or from a pre-prepared dump in PCAP format) files, certificates,
images and other media, as well as passwords and other information for authorization.
A useful feature is the search for those data sections that contain keywords
(eg user login).
Scapy
Website:
www.secdev.org/projects/scapy
Must-have for any hacker, which is the most powerful tool for
interactive packet manipulation. Receive and decode the most packets
various protocols, respond to a request, inject a modified and
hand-made package - everything is easy! With it, you can perform a whole
a number of classic tasks like scanning, tracorute, attacks and detection
network infrastructure. In one bottle, we get a replacement for such popular utilities,
like: hping, nmap, arpspoof, arp-sk, arping, tcpdump, tetheral, p0f etc. At that
same time Scapy allows you to perform any, even the most specific
a task that will never be able to do already created by another developer
means. Instead of writing a whole mountain of lines in C, so that, for example,
generate the wrong packet and fuzz some daemon, it's enough
throw a couple of lines of code using Scapy! The program has no
graphical interface, and interactivity is achieved through the interpreter
Python. Get used to it a little, and it will not cost you anything to create incorrect
packets, inject the necessary 802.11 frames, combine different approaches in attacks
(say, ARP cache poisoning and VLAN hopping), etc. The developers insist
on the fact that the capabilities of Scapy are used in other projects. Connecting her
as a module, it is easy to create a utility for various kinds of local research,
search for vulnerabilities, Wi-Fi injection, automatic execution of specific
tasks, etc.
packeth
Website:
Platform: *nix, there is a port for Windows
An interesting development that allows, on the one hand, to generate any
ethernet packet, and, on the other hand, send sequences of packets to
throughput checks. Unlike other similar tools, packeth
has a graphical interface, allowing you to create packages in the most simple way
form. Further more. Especially worked out the creation and sending
packet sequences. You can set delays between sending,
send packets at maximum speed to test throughput
section of the network (yeah, this is where they will ddos) and, what is even more interesting -
dynamically change parameters in packets (for example, IP or MAC address).
A sniffer is also called a traffic analyzer - it is a program or other hardware device that intercepts and then analyzes network traffic. Currently, these programs have a completely legal justification, therefore they are widely used on the network, but they can be used both for good and for harm.
The history of their origin goes back to the 90s, when hackers using such software could easily capture the user's login and password, which at that time were very weakly encrypted.
The word sniffer comes from the English. to sniff - sniff, the principle of action is that this program register and analyze programs that are installed on machines that transmit information packets. For the readout operation to be effective, it must be close to the host PC.
Programmers use this application for traffic analysis, other goals are pursued by hackers on the network, they just track down passwords or other information they need.
Types of traffic analyzers
Sniffers differ in types, they can be online applets or applications installed directly on a computer, which in turn are divided into hardware and software and hardware. 
Most often they are used to intercept passwords, while the application gets access to the codes of encrypted information. This can bring great inconvenience to the user, since it is not uncommon for several programs or sites to have the same password set, which ultimately leads to the loss of access to the necessary resources.
There is a type of sniffing that is used to capture a snapshot random access memory, since it is difficult to read information constantly, and at the same time not use processor power. Detect Spy It is possible by tracking the maximum file load of the PC during operation.
Another type of program works with a large data transmission channel, while the pest can generate up to 10 megabyte protocols every day.
How it works
Analyzers work only with TCP / IP protocols, such programs need a wired connection, for example, routers that distribute the Internet. Data transfer is carried out using separate packages, which, when the final goal is reached, again become a single whole. They are also able to intercept packets at any stage of transmission and get along with it valuable information in the form of insecure passwords. In any case, with the help of decryptor programs, it is possible to obtain a key even to a secure password.
The easiest way to use WiFi sniffers is in networks with weak protection - in cafes, public places, etc.
Providers through these programs can trace unauthorized access to external system addresses.
How to protect yourself from sniffers
To understand that someone has penetrated the local network, first of all, you should pay attention to package download speed, if it is significantly lower than stated, this should alert. The performance of your computer can be monitored using the Task Manager. You can use special utilities, but they most often conflict with the windows firewall, so it's best to turn it off for a while.
For system administrators, checking and searching for traffic analyzers in local network is a necessary event. To detect harmful applications, you can use well-known network antiviruses, such as Doctor Web or Kaspersky Anti-Virus, which allow you to detect pests both on remote hosts and directly inside the local network.
In addition to special applications that are simply installed on a computer, you can use more complex passwords and cryptographic systems. Cryptographic systems work directly with information, encrypting it using an electronic signature.
Application overview and main features
commview
CommView decodes the packets of transmitted information, displays the statistics of the protocols used, in the form of diagrams. The traffic sniffer allows you to analyze IP packets, and those that are needed. Sniffer for Windows works with known protocols: HTTP, HTTPS, DHCP, DDNH, DIAG, POP3, TCP, WAP, and more. CommView works with Ethernet modems, wi-fi, and more. Packets are captured through an established connection, using the " CurrentIP- connections”, where you can create address aliases. 
Tab « Packages” displays information about them, while they can be copied to the clipboard. 
« LOG-files” allows you to view packets in NFC format.
Tab « Rules". Here you can set the conditions for capturing packets. The sections on this tab are: IP Addresses, MAC Addresses, Ports, Process, Formulas, and Individual Settings.
« Warning”: provides for setting up notifications on the local network, functions using the “Add” button. Here you can set conditions, type of events:
- "Packets per second" - when the network load level is exceeded.
- "Bytes per second" - when the frequency of data transmission is exceeded.
- "Unknown address", i.e. detection of unauthorized connections.
Tab « View» - traffic statistics are displayed here.
CommView is compatible with Windows 98, 2000, XP, 2003. An Ethernet adapter is required to run the application.
Advantages: user-friendly interface in Russian, supports common types of network adapters, statistics are visualized. The only downside is the high price. 
Spynet
Spynet performs the functions of decoding packets and intercepting them. With it, you can recreate the pages visited by the user. Consists of 2 programs CaptureNet and PipeNet. It is convenient to use in the local network. CaptureNet scans data packets, the second program controls the process.
The interface is quite simple:
- Button Modify filter- setting filters.
- Button layer 2,3 – installs Flame-IP protocols; Layer 3 - TCP.
- Button pattern Matching searches for packages with the given parameters.
- Button IP— Addresses allows you to scan the necessary IP addresses that transmit information of interest. (Options 1-2, 2-1, 2=1). In the latter case, all traffic.
- Button Ports, i.e. the choice of ports.
To intercept data, it is necessary to run the Capture Start program (startup), i.e., the process of capturing data is started. The file with the saved information is copied only after the Stop command, i.e. termination of the capture action.
The advantage of Spynet is the ability to decode the web pages that the user has visited. The program can also be downloaded for free, although it is quite difficult to find. The disadvantages include a small set of features in Windows. Works in Windows XP, Vista. 
BUTTSniffer
BUTTSniffer analyzes network packets directly. The principle of operation is the interception of transmitted data, as well as the ability to automatically save them on the media, which is very convenient. This program is launched via command line. There are also filter options. The program consists of BUTTSniff.exe and BUTTSniff. dll.
Significant disadvantages of BUTTSniffer include unstable work, frequent failures up to the demolition of the OS are not uncommon ( blue screen of death).
In addition to these sniffer programs, there are many other equally well-known ones: WinDump, dsniff, NatasX, NetXRay, CooperSniffer, LanExplorter, Ne Analyzer.
There are also online sniffers (online sniffer) that, in addition to obtaining the IP address of the victim, change the IP address of the attacker directly. Those. the hacker first registers under some IP address, sends a picture to the victim's computer, which must be downloaded or email which you just need to open. After that, the hacker gets all the necessary data.
It is worth recalling that interference with the data of someone else's computer is a criminal offense.
IP Sniffer- a program that allows you to monitor packets passing through the Internet Protocol (IP). The functionality of the program includes the ability to decode packets and filter them.
In the era of modern technology and the Internet, security comes first. With the outside world, the computer exchanges digital information through special protocols. Internet Protocol (IP) is one of the most popular and popular due to its security and high data transfer speed.
It was with his advent, in 1981, that computers got the opportunity to send messages to each other in the form of data packets. Sniffer for Windows is designed to monitor traffic and check the contents of packets. Thus, this utility is an additional way to secure your computer. Download IP Sniffer is best solution, keep traffic and all information flows under control.


Download IP Sniffer for free
IP Sniffer for Windows (1.4 MB)
IP Sniffer Key Features:
- Multifunctionality;
- Safety;
- Small size;
- Intuitive interface.
The latest version of the sniffer has a convenient and simple interface. The program allows you to view which IP addresses are most often used, which are most often connected to your machine. You can conveniently monitor the amount of traffic. You can also forcefully end a particular connection using the Netstat function. Downloading a sniffer to a computer is recommended if the user is faced with the task of intercepting traffic between hosts. This allows you to do the Snoofing function, which, among many, supports the popular ARP protocol. Also popular functions of a sniffer in Russian are network ping, the ability to convert an IP address to a Hostname and vice versa, and a search for DHCP servers. It can also be used to get Netbios data for the specified IP address.
Downloading a sniffer for free is recommended if the user wants to get a reliable assistant in traffic control. The program does not need to be installed and additional setting. You can use it immediately after downloading. The program interface is concise and simple. Windows and tabs are arranged so that it is as convenient and comfortable to use as possible. The developer is constantly improving and improving his product. Updates are released regularly. The program is highly resistant to any malicious influences. Our portal provides all visitors with the opportunity to download the sniffer program without registration and SMS.