Information protection system from insiders pdf. Protection of information from insiders using software tools. Zgate: Internet Leak Protection
In the field of information security, organizations tend to pay the most attention to protection against external attacks, so almost all funds allocated for security are directed to protecting vulnerable points of the enterprise network perimeter. The current situation has found a corresponding reflection in the IT security solutions market - in recent years, a wide range of different means of protection against viruses, worms, Trojans and other external threats has been offered.
Gradually, however, enterprises begin to realize a new danger. It does not come from hackers, not from spam or random viruses, but from our own employees. Insiders are inside the organization itself and are endowed with completely legal powers, so it is much easier for them to gain access to the information they are interested in than for any attacker from the outside. To better understand the problem, let's turn to a study conducted in 2006 by the American analytical company Aberdeen Group "The Insider Threat Benchmark Report - Strategies for data protection”, during which 88 large American corporations were interviewed.
Main results of the survey of large corporations
The threat from insiders is growing. Modern business can no longer ignore this danger and is intensively preparing to counter it. Companies that choose not to notice it or skimp on the introduction of new security systems suffer serious losses. Many of the companies mentioned in the study suffered severely from data breaches and only then took care of preventive measures. Their example should serve as a lesson for other firms.
Businesses that want to protect themselves from leaks of confidential information should take a responsible approach to solving the problem. Irrational savings on security means will result in solid losses in the near future. The best option would be to enlist the help of professionals who specialize in insider protection systems. Such systems can be easily integrated into existing infrastructure. In addition, vendors will not only ensure that the solution works, but also guarantee its high efficiency.
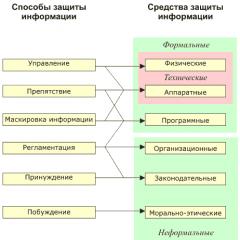
As such, there is no remedy against insiders. Only the application of a whole range of measures and solutions will help to reliably protect information. Despite the inertia of large suppliers, there are a sufficient number of ready-made complexes on the market that provide protection against insiders and leaks.
One of the most important modern information security technologies is network traffic filtering (already implemented by 53% of respondents). Another 28% plan to install similar filters this year. In addition, data classification is a very promising technology. Although today only 42% of corporations use it, this year their number will increase by 44% (that is, up to 86%). However, it is a matter of serious concern that an unreasonably low number of respondents use other effective solutions to protect against leaks and insiders, such as monitoring the actions of employees.
For many enterprises, one of the main obstacles (44%) to the introduction of additional means of protection against information leaks is the limited IT resources. At the same time, the introduction of such protection tools can not only significantly reduce the risk of losing important data, but also significantly (by 17.5%) reduce the costs of IT departments.
current position
There is nothing surprising in the fact that the consequences of insider incidents are often much more deplorable than even a successful hacker attack. There are many reasons for this. The ease of access to various information resources alone cannot explain everything. The fact is that the information stolen by insiders is usually more important than that which hackers can get. One of the biggest reasons for the rise in the insider threat and the ease with which they commit illegal acts is the negligence of internal IT security services (if any exist). Organizations are not ready to confront insiders, because they simply do not have the appropriate tools. Even if the threat is identified, the workers in the sphere without danger still cannot properly resist it, since they have not gained the necessary experience in this area. In general, complex solutions for protecting confidential information from insiders can already be found on the market. Unfortunately, often responsible leaders do not understand the gravity of the threat. By inertia, they continue to build up efforts to protect the perimeter of their organization precisely from external danger.
Meanwhile, news agencies and the media are paying more and more attention to the problem of insiders. Experts talk about an increase in the number of leaks of confidential information and their sad consequences: loss of time, financial losses and a blow to reputation. In addition, there is a global trend that business is starting to switch to the problem of internal IT security.
During the study "The Insider Threat Benchmark Report - Strategies for Data Pro tection", analysts managed to find out that over the past year, many suppliers and distributors of IT systems have qualitatively changed the range of proposed solutions. At the same time, the share of products designed specifically to combat insiders has increased. However, at the same time, the largest IT vendors continue to expand their traditional range, keeping the proportions of solutions at the same level. This indicates either an underestimation of the potential of the corresponding product line, or a small current demand. However, 41% of US respondents have already implemented security measures in their IT infrastructure in one way or another problem solving insiders.
Note that Russian customers can see for themselves that the interest in systems to combat leaks and insiders on the part of suppliers and system integrators has greatly increased. For example, Kaspersky Lab has separated its business in the field of internal IT security into a separate company - InfoWatch, and almost all Russian system integrators have included solutions from this company in their product line. According to Denis Zenkin, marketing director of InfoWatch, in 2005 the company's profit increased by 120% and in 2006 a similar picture was observed. And this despite the fact that Russian companies significantly behind the US in the use of systems to protect against insiders. According to the study "Internal IT Threats in Russia 2005", during which InfoWatch surveyed more than 300 domestic organizations, only 2% of respondents use systems to combat insiders and leaks. However, the growth of suppliers' profits clearly indicates that this situation is gradually changing.
In addition, another major anti-virus company, McAfee, has recently shown interest in systems to combat insiders. In October 2006, it bought Israeli firm Onigma, whose only solution is to detect and prevent leaks. According to the press release, McAfee will integrate Onigma technologies into its own solution and thus begin its expansion into the internal IT security market.
It is possible that in the near future the largest IT security company, Symantec, will appear on the market for leak protection products. In general, we can safely say that the inclusion of products to combat insiders in your range is an extremely promising direction for diversification for all links in the distribution chain of IT security solutions.
View from the other side
Let's return now to the results of the study "The Insider Threat Benchmark Report - Strategies for Data Protection" and look at the systems of protection against insiders and leaks through the eyes of the customer. All American companies can be conditionally divided into three unequal groups: laggards (30%), middling (50%) and leaders (20%). The performance indicators of the lagging enterprises are generally lower than the industry average, while those of the leaders are correspondingly higher. It turns out that absolutely all successful organizations (100% of respondents) consider the protection of confidential data the most important area in the fight against insiders. In addition, the best companies use identification and access control policies much more widely (75%). The characteristics of different groups in the field of internal IT security are presented in the figure.
It can be seen from the charts that leading companies prefer to consider the project of introducing an insider protection system as a full-fledged business task. At the same time, they attach special importance to the complex of accompanying services. This allows you to build the most effective internal security system and not shift atypical tasks onto the shoulders of your own employees. In addition, the best companies in their industry are trying to minimize the human factor through the use of fully automated processes. Finally, leaders prioritize the integration of products into a single and manageable system, so they appreciate the flexibility of the implemented insider protection solution.
Let's try to evaluate the problem of internal security in terms of technology (Table 1). After studying several industries, it turned out that the main technologies used are: passwords, identification systems, biometrics, network traffic scanning and user access control to confidential information.
Table 1. Security protection technologies: current state and forecast
|
Technology |
Share of respondents using the technology now, % |
Share of respondents planning to implement technology in the next 12 months, % |
|
Complex passwords |
||
|
Access Control Lists |
||
|
Network traffic filtering |
||
|
Perimeter Scan |
||
|
Automatic monitoring of employee access |
||
|
Data classification (according to the degree of confidentiality) |
||
|
Single point of entry |
||
|
Identification with challenge and confirmation |
||
|
Authentication via callback to mobile phone |
Exactly 50% of the industry's best firms use complex passwords, network traffic filtering, and access control lists. Moreover, companies intend to significantly increase the use of these technologies. Thus, the share of complex passwords will increase by 26% and reach 93%; the popularity of access control lists will increase by 24% and reach the mark of 90%, and the share of network traffic filtering will increase from 53 to 81%. Meanwhile, the use of ID-cards, despite their prevalence at the present time, can hardly be considered a popular trend. Only 13% of respondents plan to implement this technology this year.
Curiously, the most promising technologies are automatic monitoring of employees' access to important data (up to 72% is expected) and data classification (from 42% in 2006 to 86% today). Here the results of the study coincide with the opinion of domestic experts in the field of information security. The InfoWatch analytical center believes that companies have paid unfairly little attention to the automatic monitoring of insider actions and data classification in recent years. Meanwhile, without this, it is simply impossible to build a reliable protection system.
Further, according to the survey, the same 53% who use traffic filtering believe that perimeter protection alone is not sufficient for internal security. It is necessary, among other things, to develop virtual private networks so as not to reduce the level of security when communicating with external partners.
These technologies provide a layered approach and improve the security of sensitive data. However, in addition to the technological side, one should not forget about the banal physical safety of information. There are many examples of how important documents fell into the hands of intruders after breaking into an office and stealing computer equipment. What's more, backup tapes and mobile media with sensitive content are often lost in transit or on business trips.
Insider Protection
Currently, there is no single established point of view on how to regulate user access. This forces organizations to provide centralized data management in a distributed environment. Technology can make governability, accountability, and data security possible, but it needs to be applied properly. In turn, the methods of use depend on the specifics of the activity of the customer enterprise. Therefore, it is required to conduct a deep and comprehensive analysis of the IT infrastructure on which the security system is supposed to be deployed. Many customers absolutely rightly entrust the process of evaluating and selecting technologies to specially created groups, which include specialists from various fields.
Modern technologies and methods of counteracting insiders differ significantly. The fact is that suppliers cannot offer a universal remedy from insiders. They provide a range of solutions for identifying outliers, classifying data by degree of confidentiality, and restricting access.
While only 51% of companies surveyed in the survey believe that comprehensive insider protection solutions are critical, the remaining 49% do not value their role as highly. However, the significance of this result lies in the fact that at least half of the respondents prefer complex solutions. This suggests that they are really concerned about this problem and understand the importance of joint measures.
In addition, in some industries, members are required to be more sensitive to the confidentiality of customer data. Constantly changing legislation at the federal and regional levels pays more and more attention to the protection of personal information (such as full name, date of birth, home address, credit card numbers, medical policy, etc.).
Organizations must recognize the importance of legislative provisions in the area of personal protection. According to the survey participants, in order to improve management, it is necessary to automate authorized access. Companies that do not automate access control lists, data preparation, and classification can face serious problems. Thus, 78% of respondents consider information protection the most important reason for building insider protection. So, businesses are just beginning to recognize the insider threat and, for various reasons, tend to play down the importance of internal incidents. However, it is impossible to hide the trend of increasing danger from insiders.
Challenges to Implementing Insider Protection
Consider two more interesting results of the study. In table. Table 2 shows the five most serious, according to the respondents, problems that arise when implementing a system of protection against internal threats, as well as options for their solution. Tab. 3 is similar to table. 2 in terms of structure, but compiled on the basis of answers from respondents belonging to the group of leading companies. Comparing the data obtained, it is easy to notice the differences in the approach to this problem of the middle peasants and the most successful business representatives. If for leaders the main problem is the imposition of the implemented solution on already used technologies (75%), then for all respondents in general it is the limited IT resources (44%). During the study, it turned out that advanced organizations have already implemented comprehensive protection of their IT infrastructure and thus covered the network itself, and also secured themselves at the application level. Now these companies are looking for ways to strengthen the established security system. Organizations, for which the main problem is limited IT resources, are seriously limited in their actions. This is worrisome, as saving on security can lead to much larger losses. Obviously, IT services, like IT security services, must receive full funding. After all, they are preparing a base on which all other units will successfully function.
Table 2. The most serious problems in the implementation of insider protection systems
and them Possible Solution(based on all respondents)
|
Problem |
Share of responses, % |
Solution to the problem |
Share of responses, % |
|
Limited IT resources to implement and manage the solution |
Determine requirements prior to implementation |
||
|
The complexity of the software solution |
Determine the owners of data and processes |
||
|
Overlay solution on existing processes |
Provide training on the use of new processes and procedures |
Analyzing the tables, we can also note the following rather interesting fact: the personnel of leading companies show their dissatisfaction with innovations much more often than employees of medium-sized enterprises (50 vs. 38%). However, there is nothing surprising in this. In the field of IT security, the human factor is at least half the problem. If, for example, an organization allows contractors, partners or suppliers to use its network, but does not care about the procedures for regulating access to information, then we can safely say that it will definitely have problems in this direction.
Table 3. The most serious problems in the implementation of insider protection systems
and their possible solution (based on leading companies)
|
Problem |
Share of responses, % |
Solution to the problem |
Share of responses, % |
|
Overlaying the solution on already implemented technologies |
Focus on short projects with quick returns |
||
|
Employee resistance to innovation |
Gradually phase out and slowly distribute new solutions to users |
||
|
Lack of funds for activities |
Implement top-down, from the technical and IT department to all other departments |
||
|
Limited IT resources to implement and manage the solution |
Demonstrate the capabilities and features of solutions to the heads of departments |
||
|
Poor knowledge of risk assessment tools |
Provide training on the use of new processes and procedures |
In general, the lagging companies and the middle peasants, unlike the leaders, use automation and integration of solutions to a lesser extent, and in addition, they have inexperienced employees on their staff. All this affects the effectiveness of the analysis of security procedures and the interpretation of its results. Often, only the introduction of automated processes and staff development leads to overcoming the human factor. According to the study, about 25% of the best enterprises use fully automated systems. At the same time, only 9% of automation cases can be attributed to the industrial one.
Information security increases as new technologies are used in accordance with business requirements. Continuous improvement of protection systems will bring undoubted benefits. According to the study, organizations that implemented insider protection systems experienced the following effects on average:
- complaints and appeals to IT departments and support service decreased by 3.5%;
- the number of IT security incidents decreased by 13%;
- reduced labor costs in IT departments - by 17.5%.
Thus, analysts come to the conclusion that organizations that deal only with external protection are doomed to failure. Indeed, security at the perimeter of an organization helps to repel hackers, while companies that implement leak and insider protection systems actually manage to reduce the number of incidents and reduce IT costs.
Conclusion
Based on the results of the conducted research and assessment of the situation, the following conclusions arise. First, there is no single technology for protecting against insiders. Only a set of measures can ensure security properly. Disparate products, no matter how good they are, certainly will not solve the problems that arise when building comprehensive protection. Yes, it is possible to close one of the directions, but the difficulty lies in the fact that there are a huge number of different threats. Attackers act in various ways, and just in order to eliminate all possible loopholes, it is necessary to create a multi-level system.
Secondly, the responsibility for the safety of confidential information cannot be assigned to one person or even to a unit. In this direction, employees of the IT service and the IT security department should work closely. An even more effective way is to involve specialists with extensive experience in the field of leak protection. The latter offer a deep analysis of the existing situation and provide the customer with specific solutions. A reliable system is being built, which can be maintained by the company's personnel with the necessary support of the integrator.
Thirdly, the data available in the organization needs to be carefully studied and structured according to the degree of confidentiality. Then, based on this classification, an access restriction system should be built. Users should not have access to data that they do not need to perform their official duties. In addition, it is necessary to periodically review access rights to keep the system of differentiation up to date.
Fourthly, the human factor is one of the critical ones in the information security system. Unfortunately, it is people who become the weakest link in the chain. Often, insiders are employees responsible, if not for protecting confidential information, then at least for maintaining the confidentiality of information. Out of ignorance or distraction, with or without malicious intent, but it is they who can bring significant harm to their employers. Much more dangerous is the situation when the insider is a person from the IT department or from the IT security service. His authority, of course, is much broader than that of most other employees, and he has sufficient knowledge and capabilities to quietly “merge” data. It is for these reasons that for the successful conduct of business it is required to use professional systems for monitoring the actions of employees. They should be as automated as possible, not dependent on a person, so that it is possible to control the employee. Software solutions and complexes are the most effective method of protecting against the increased threat from insiders. Of course, we should not forget about the methods of working with employees. They should be educated about the need to comply with security standards and require them to comply with existing privacy directives. However, only software and hardware is able to prevent possible cases of internal theft.
Recent studies in the field of information security, such as the annual CSI / FBI Computer Crime And Security Survey, have shown that the financial losses of companies from most threats are decreasing year by year. However, there are several risks, the losses from which are increasing. One of them is the deliberate theft of confidential information or violation of the rules for handling it by those employees whose access to commercial data is necessary for the performance of official duties. They are called insiders.
In the vast majority of cases, the theft of confidential information is carried out using mobile media: CDs and DVDs, ZIP devices and, most importantly, all kinds of USB drives. It was their mass distribution that led to the flourishing of insiders around the world. The leaders of most banks are well aware of what threatens, for example, if a database with personal data of their clients or, moreover, transactions on their accounts, falls into the hands of criminal structures. And they are trying to fight the possible theft of information with the organizational methods available to them.
However, organizational methods in this case are ineffective. Today it is possible to organize the transfer of information between computers using a miniature flash drive, cell phone, trz-plssra, digital camera ... Of course, you can try to ban all these devices from being brought into the office, but this, firstly, will negatively affect relations with employees , and secondly, it is still very difficult to establish really effective control over people - the bank is not mailbox". And even disabling all devices on computers that can be used to write information to external media (FDD and ZIP drives, CD and DVD drives, etc.) and USB ports will not help. After all, the former are needed for work, and various peripherals are connected to the latter: printers, scanners, etc. And no one can prevent a person from turning off the printer for a minute, inserting a flash drive into the vacated port and copying important information to it. You can, of course, find original ways of protection. For example, in one bank they tried this method of solving the problem: they filled the junction of the USB port and the cable with epoxy resin, tightly “tying” the latter to the computer. But, fortunately, today there are more modern, reliable and flexible methods of control.
The most effective means of minimizing the risks associated with insiders is special software that dynamically manages all devices and computer ports that can be used to copy information. The principle of their work is as follows. Permissions to use different ports and devices are set for each user group or for each user individually. The biggest advantage of such software is flexibility. You can enter restrictions for specific types of devices, their models and individual instances. This allows you to implement very complex policies for the distribution of access rights.
For example, some employees can be allowed to use any printers and scanners connected to USB ports. All other devices inserted into this port will remain inaccessible. If the bank uses a user authentication system based on tokens, then in the settings you can specify the key model used. Then users will be allowed to use only devices purchased by the company, and all others will be useless.
Based on the principle of operation of protection systems described above, you can understand what points are important when choosing programs that implement dynamic blocking of recording devices and computer ports. First, it's versatility. The protection system should cover the entire range of possible ports and information input-output devices. Otherwise, the risk of commercial information theft remains unacceptably high. Secondly, the software in question should be flexible and allow you to create rules using a large amount of various information about devices: their types, model manufacturers, unique numbers that each instance has, etc. And, thirdly, the insider protection system should be able to integrate with the information system of the bank, in particular with Active Directory. Otherwise, the administrator or security officer will have to maintain two databases of users and computers, which is not only inconvenient, but also increases the risk of errors.
Recent studies in the field of information security, such as the annual CSI/FBI ComputerCrimeAndSecuritySurvey, have shown that the financial losses of companies from most threats are decreasing year by year. However, there are several risks, the losses from which are increasing. One of them is the deliberate theft of confidential information or violation of the rules for handling it by those employees whose access to commercial data is necessary for the performance of official duties. They are called insiders.
In the vast majority of cases, the theft of confidential information is carried out using mobile media: CDs and DVDs, ZIP devices and, most importantly, all kinds of USB drives. It was their mass distribution that led to the flourishing of insider trading around the world. The leaders of most banks are well aware of what threatens, for example, if a database with personal data of their clients or, moreover, transactions on their accounts, falls into the hands of criminal structures. And they are trying to fight the possible theft of information with the organizational methods available to them.
However, organizational methods in this case are ineffective. Today it is possible to organize the transfer of information between computers using a miniature flash drive, a cell phone, an mp3 player, a digital camera... Of course, you can try to ban all these devices from being brought into the office, but this, firstly, will negatively affect relations with employees , and secondly, it is still very difficult to establish really effective control over people - the bank is not a "mailbox". And even disabling all devices on computers that can be used to write information to external media (FDD and ZIP drives, CD and DVD drives, etc.) and USB ports will not help. After all, the former are needed for work, and various peripherals are connected to the latter: printers, scanners, etc. And no one can prevent a person from turning off the printer for a minute, inserting a flash drive into the vacated port and copying important information to it. You can, of course, find original ways of protection. For example, in one bank they tried this method of solving the problem: they filled the junction of the USB port and the cable with epoxy resin, tightly “tying” the latter to the computer. But, fortunately, today there are more modern, reliable and flexible methods of control.
The most effective means of minimizing the risks associated with insiders is special software that dynamically manages all devices and computer ports that can be used to copy information. The principle of their work is as follows. Permissions to use different ports and devices are set for each user group or for each user individually. The biggest advantage of such software is flexibility. You can enter restrictions for specific types of devices, their models and individual instances. This allows you to implement very complex policies for the distribution of access rights.
For example, some employees can be allowed to use any printers and scanners connected to USB ports. All other devices inserted into this port will remain inaccessible. If the bank uses a user authentication system based on tokens, then in the settings you can specify the key model used. Then users will be allowed to use only devices purchased by the company, and all others will be useless.
Based on the principle of operation of protection systems described above, you can understand what points are important when choosing programs that implement dynamic blocking of recording devices and computer ports. First, it's versatility. The protection system should cover the entire range of possible ports and information input-output devices. Otherwise, the risk of commercial information theft remains unacceptably high. Secondly, the software in question should be flexible and allow you to create rules using a large amount of various information about devices: their types, model manufacturers, unique numbers that each instance has, etc. And, thirdly, the insider protection system should be able to integrate with the bank's information system, in particular with ActiveDirectory. Otherwise, the administrator or security officer will have to maintain two databases of users and computers, which is not only inconvenient, but also increases the risk of errors.
Protection of information from insiders using software tools
Alexander Antipov
I hope that the article itself, and especially its discussion, will help identify various nuances of using software tools and become a starting point in developing a solution to the described problem for information security specialists.
nahna
The marketing division of Infowatch has been convincing all interested parties - IT specialists, as well as the most advanced IT managers for a long time, that most of the damage from a violation of the company's information security falls on insiders - employees who disclose trade secrets. The goal is clear - it is necessary to create demand for the manufactured product. Yes, and the arguments look quite solid and convincing.
Formulation of the problem
Build a system for protecting information from theft by personnel in a LAN based on Windows 2000/2003 Active Directory. User workstations under Windows control xp. Enterprise management and accounting based on 1C products.Secret information is stored in three ways:
- DB 1C - network access via RDP (terminal access);
- shared folders on file servers - network access;
- locally on the employee's PC;
What's on the market
I divided the systems under consideration into three classes:- Systems based on context analyzers - Surf Control, MIME Sweeper, InfoWatch Traffic Monitor, Dozor Jet, etc.
- Systems based on static device locking - DeviceLock, ZLock, InfoWatch Net Monitor.
- Systems based on dynamic blocking of devices - SecrecyKeeper, Strazh, Akkord, SecretNet.
Systems based on context analyzers
Principle of operation:The transmitted information is searched for keywords, based on the results of the search, a decision is made on the need to block the transmission.
In my opinion, InfoWatch Traffic Monitor (www.infowatch.ru) has the maximum potential among the listed products. The well-proven Kaspersky Antispam engine, which most fully takes into account the peculiarities of the Russian language, is taken as a basis. Unlike other products, InfoWatch Traffic Monitor, when analyzing, takes into account not only the presence of certain lines in the data being checked, but also the predefined weight of each line. Thus, when making a final decision, not only the occurrence of certain words is taken into account, but also the combinations in which they occur, which allows increasing the flexibility of the analyzer. Other features are standard for such products - analysis of archives, MS Office documents, the ability to block the transfer of files of unknown format or password-protected archives.
Disadvantages of the considered systems based on contextual analysis:
- Only two protocols are controlled - HTTP and SMTP (for InfoWatch Traffic Monitor, and for HTTP traffic, only data transmitted using POST requests is checked, which allows organizing a leak channel using data transmission using the GET method);
- Data transfer devices - floppy disks, CDs, DVDs, USB disks, etc. are not controlled. (Infowatch has InfoWatch Net Monitor for this case).
- to bypass systems built on the basis of content analysis, it is enough to use the simplest text encoding (for example: secret -> s1e1k1r1e1t), or steganography;
- the following task is not solved by the method of content analysis - a suitable formal description does not come to mind, so I’ll just give an example: there are two Excel files - in the first retail prices(public information), in the second - wholesale for a specific client (secret information), the contents of the files differ only in numbers. These files cannot be distinguished using content analysis.
contextual analysis is only suitable for creating traffic archives and counteracting accidental information leakage, and does not solve the task.
Systems based on static blocking of devices
Principle of operation:users are assigned access rights to controlled devices, similar to file access rights. In principle, almost the same effect can be achieved using standard Windows mechanisms.
Zlock (www.securit.ru) - the product appeared relatively recently, so it has minimal functionality (I don’t think it’s frills), and it doesn’t differ in debugging, for example, the control console sometimes crashes when trying to save settings.
DeviceLock (www.smartline.ru) is a more interesting product, it has been on the market for a long time, so it works much more stable and has more diverse functionality. For example, it allows shadow copying of transmitted information, which can help in the investigation of an incident, but not in its prevention. In addition, such an investigation is likely to be carried out when the leak becomes known, i.e. a considerable period of time after it occurs.
InfoWatch Net Monitor (www.infowatch.ru) consists of modules - DeviceMonitor (analogous to Zlock), FileMonitor, OfficeMonitor, AdobeMonitor and PrintMonitor. DeviceMonitor is an analogue of Zlock, standard functionality, without raisins. FileMonitor - control of access to files. OfficeMonitor and AdobeMonitor allow you to control how files are handled in their respective applications. It is currently quite difficult to come up with a useful, and not a toy, application for FileMonitor, OfficeMonitor and AdobeMonitor, but in future versions it should be possible to contextually analyze the data being processed. Perhaps then these modules will reveal their potential. Although it is worth noting that the task of contextual analysis of file operations is not trivial, especially if the content filtering base is the same as in Traffic Monitor, i.e. network.
Separately, it is necessary to say about protecting the agent from a user with local administrator rights.
ZLock and InfoWatch Net Monitor simply lack such protection. Those. the user can stop the agent, copy the data, and start the agent again.
DeviceLock has such protection, which is a definite plus. It is based on intercepting system calls for working with the registry, file system and process management. Another plus is that protection works in safe-mode as well. But there is also a minus - to disable protection, it is enough to restore the Service Descriptor Table, which can be done by loading a simple driver.
Disadvantages of the considered systems based on static blocking of devices:
- The transmission of information to the network is not controlled.
- -Can't distinguish between classified and non-secret information. It works on the principle that either everything is possible or nothing is impossible.
- There is no or easily bypassed protection against unloading the agent.
it is not advisable to introduce such systems, because they don't solve the problem.
Systems based on dynamic blocking of devices
Principle of operation:access to transmission channels is blocked depending on the user's access level and the degree of secrecy of the information being worked with. To implement this principle, these products use the mechanism of authoritative access control. This mechanism is not very common, so I will dwell on it in more detail.
Authoritative (forced) access control, in contrast to descriptive (implemented in the security system of Windows NT and higher), consists in the fact that the owner of a resource (for example, a file) cannot weaken the requirements for access to this resource, but can only strengthen them within your level. The requirements can be relaxed only by a user endowed with special powers - an officer or information security administrator.
The main goal of developing products such as Guard, Accord, SecretNet, DallasLock and some others was the possibility of certification of information systems in which these products will be installed, for compliance with the requirements of the State Technical Commission (now FSTEC). Such certification is obligatory for information systems in which the state is processed. secret, which basically ensured the demand for products from state-owned enterprises.
Therefore, the set of functions implemented in these products was determined by the requirements of the relevant documents. Which, in turn, led to the fact that most of the functionality implemented in the products either duplicates the standard Windows functionality (clearing objects after deletion, clearing RAM), or uses it implicitly (describing access control). And the developers of DallasLock went even further, implementing the mandatory access control of their system, through the Windows description control mechanism.
The practical use of such products is extremely inconvenient, for example, DallasLock requires repartitioning for installation. hard drive, which also needs to be performed using third-party software. Very often, after certification, these systems were removed or turned off.
SecrecyKeeper (www.secrecykeeper.com) is another product that implements an authoritative access control mechanism. According to the developers, SecrecyKeeper was developed specifically to solve a specific problem - preventing information theft in a commercial organization. Therefore, again, according to the developers, during the development, special attention was paid to simplicity and ease of use, both for system administrators and for ordinary users. How successful this is is for the consumer to judge, i.e. US. In addition, SecrecyKeeper implements a number of mechanisms that are not available in the other systems mentioned - for example, the ability to set the security level for resources with remote access and the agent protection mechanism.
Information movement control in SecrecyKeeper is implemented on the basis of the Information Secrecy Level, User Permission Levels and Computer Security Level, which can take the values public, secret and top secret. The Information Confidentiality level allows classifying the information processed in the system into three categories:
public - not secret information, there are no restrictions when working with it;
secret - secret information, when working with it, restrictions are introduced depending on the User Permission Levels;
top secret - top secret information, when working with it, restrictions are introduced depending on the User Permission Levels.
The Security Level of Information can be set for a file, network drive and the port of the computer on which some service is running.
User Permission Levels allow you to determine how a user can move information, depending on its Privacy Level. The following User Access Levels exist:
User Access Level - limits the maximum Security Level of Information to which an employee can access;
Level of Access to the Network - limits the maximum Level of Secrecy of Information that an employee can transmit over the network;
Removable Media Access Level - limits the maximum Security Level of Information that an employee can copy to external media.
Printer Security Level - limits the maximum Security Level of Information that an employee can print.
Computer Security Level - determines the maximum Security Level of Information that can be stored and processed on a computer.
Access to information with a level of secrecy public, can be carried out by an employee with any level of access. Such information can be transmitted over the network without restrictions and copied to external media. The history of working with information with the public secret level is not tracked.
Access to information with a secret level of secret can only be obtained by employees whose clearance level is secret or higher. Only employees whose access level to the network is secret or higher can transfer such information to the network. Copying such information to external media can only be done by employees whose removable media access level is secret or higher. Printing such information can only be done by employees whose printer access level is secret or higher. The history of working with information that has a secret level of secret, i.e. attempts to access it, attempts to transfer it over the network, attempts to copy it to external media or print it are logged.
Access to information with a top secret level can only be obtained by employees whose clearance level is equal to top secret. Only employees whose access level to the network is equal to the top secret can transfer such information to the network. Copying such information to external media can only be done by employees whose removable media access level is equal to the top secret. Only employees with a printer access level equal to top secret can print such information. The history of working with information that has a top secret level of secrecy, i.e. attempts to access it, attempts to transfer it over the network, attempts to copy it to external media or print it are logged.
Example: let an employee have a Security Level of top secret, a Network Security Level of secret, a Removable Media Security Level of public, and a Printer Security Level of top secret; in this case, the employee can access a document with any level of secrecy, the employee can transfer information with a secrecy level no higher than secret to the network, copy, for example, to floppy disks, the employee can only information with the public secrecy level, and the employee can print any information on a printer .
To control the dissemination of information to the enterprise, each computer assigned to an employee is assigned a Computer Security Level. This level limits the maximum Information Security Level that any employee can access from this computer, regardless of the employee's clearance levels. That. if an employee has a Permission Level equal to top secret, and the computer on which he is currently working has a Security Level equal to public, then the employee will not be able to access information with a secret level higher than public from this workstation.
Armed with theory, let's try to use SecrecyKeeper to solve the problem. To describe in a simplified way the information processed in information system of the abstract enterprise under consideration (see the problem statement), you can use the following table:
The employees of the enterprise and the area of their job interests are described using the second table:
Let the following servers be used in the enterprise:
Server 1C
File server with balls:
SecretDocs - contains secret documents
PublicDocs - contains public documents
I note that for the organization of standard access control, the standard capabilities of the operating system and application software are used, i.e. in order to prevent, for example, a manager from accessing the personal data of employees, no additional security systems need to be introduced. We are talking about counteracting the dissemination of information to which the employee has legal access.
Let's proceed to the direct configuration of SecrecyKeeper.
I will not describe the process of installing the management console and agents, everything is as simple as possible - see the documentation for the program.
System setup consists of performing the following steps.
Step 1. Install agents on all PCs except servers - this immediately prevents them from getting information for which the Security Level is set higher than public.
Step 2. Assign clearance levels to employees according to the following table:
| User Clearance Level | Network Access Level | Removable Media Access Level | Printer Access Level | |
| director | secret | secret | secret | secret |
| manager | secret | public | public | secret |
| personnel officer | secret | public | public | secret |
| accountant | secret | public | secret | secret |
| Secretary | public | public | public | public |
Step 3. Assign Computer Security Levels as follows:
Step 4. Configure Information Privacy Levels on Servers:
Step 5. Set up Privacy Levels on Employees' PCs for Local Files. This is the most time-consuming part, since it is necessary to clearly understand which of the employees works with what information and how critical this information is. If an information security audit has been conducted in an organization, its results can greatly facilitate the task.
Step 6. If necessary, SecrecyKeeper allows you to limit the list of programs allowed to run by users. This mechanism is implemented independently of the Windows Software Restriction Policy and can be used if, for example, it is necessary to impose restrictions on users with administrator rights.
Thus, with the help of SecrecyKeeper, it is possible to significantly reduce the risk of unauthorized distribution of secret information - both leakage and theft.
Disadvantages:
- difficulty with the initial setting of privacy levels for local files;
General conclusion:
maximum opportunities for protecting information from insiders are provided by software that has the ability to dynamically regulate access to information transmission channels, depending on the degree of secrecy of the information with which the work is being done and the level of employee access.
Company is a unique service for buyers, developers, dealers and affiliate partners. In addition, this is one of the best online software stores in Russia, Ukraine, Kazakhstan, which offers customers a wide range of products, many payment methods, prompt (often instant) order processing, tracking the order fulfillment process in the personal section.
According to various analytical companies, information leakage very often occurs not due to its theft from the outside, but due to the transfer of confidential information by their own employees to representatives of competing organizations. Today, there are many different devices to which any documents stored in local network organizations.
According to various analytical companies, information leakage very often occurs not due to its theft from the outside, but due to the transfer of confidential information by their own employees to representatives of competing organizations. Today, there are many different devices to which any documents stored on the organization's local network can be copied. And it's not just external USB drives or CD/DVD drives. You can also copy information to mp3 players, Cell Phones, which may or may not connect directly to a computer, to external equipment that can connect to a local network via Wi-Fi and in other ways. In addition, this is sending by e-mail, by means of instant messaging programs, through forums, blogs, and chats. There are many options, is it possible to protect yourself from them?
For protection of data from insiders apply various methods, which include the use of special programs designed to control the use peripherals. In this article, we will consider several programs, both foreign manufacturers and domestic ones, and try to determine where and when they should be applied.
The program is designed for access restrictions to various peripheral devices, with the ability to create "white" lists, monitor user activity, shadow copy files copied to or from controlled devices. It is possible to install tracking drivers both centrally and locally.
The application can be installed both centrally and locally if access to the protected computer via the network is limited or impossible. A single distribution kit includes several modules: server, installed on the server of the office local network allows / prohibits certain actions, saves information to the database; client, implemented as a tracking driver; administrator and database, which is used as SQLite.
Tracking drivers provide control various ports, including USB, CIM, LPT, WiFi, IR and others. Depending on the port type, you can deny access completely, allow reading, or allow full access to the device. There is no distribution of access over time. It was also noted that when allowing read-only access to devices such as USB flash drives, the ability to edit ordinary text files on these devices with the ability to save them on the same media remains.
Shows USB devices connected to computers and keeps a log of user actions with external storage drives. Information about the connection/disconnection time of devices and about which files and when were read or written is stored in the database. Implemented shadow copying of files that were read from or written to USB devices. There is no shadow copying of files sent for printing or other devices, they are only logged.
There is a concept of a "white list", which includes USB devices, access to which must always be open on all computers (for example, USB keys). This list is the same for all computers; there are no individual lists for individual users.
 provides configuration of access to various external devices, but does not select printers connected to these ports from the general list of USB devices. At the same time, it distinguishes between removable media and can set different types of access for them. Removable media is automatically added to the device database (the program will add to the database all USB drives that have ever been connected to a particular computer), which allows you to apply the access rights assigned to them for any computers protected by the program.
provides configuration of access to various external devices, but does not select printers connected to these ports from the general list of USB devices. At the same time, it distinguishes between removable media and can set different types of access for them. Removable media is automatically added to the device database (the program will add to the database all USB drives that have ever been connected to a particular computer), which allows you to apply the access rights assigned to them for any computers protected by the program.
It has the ability to use the centralized installation of client parts using Active Directory Group Policy. At the same time, you can install them locally and through the program administrator panel. Differentiation of access rights is carried out on the basis of access control policies, however, it is possible to create several policies that can be applied individually for different computers. In addition to the access control function, it allows logging the use of devices on the local computer.
The program supports the shadow copy function - the ability to save an exact copy of files copied by the user to external storage devices. Exact copies of all files are stored in a special storage and can later be analyzed using the built-in analysis system. Shadow copying can be set for individual users and user groups. When the "keep only log" function is enabled, when copying files, only information about them will be saved (without saving an exact copy of the file).
The program does not have the concept of a "white list" of devices. Instead, you can specify removable media in the general policy and allow access to it from any computer. Note that there is no way to apply the same settings to individual CD/DVDs.
 Company program GFI significantly surpasses in its capabilities and , and - in it, for example, there are much more controlled devices than previous programs (iPod media players, Creative Zen, mobile phones, digital cameras, tape and Zip archiving tools, webcams, scanners).
Company program GFI significantly surpasses in its capabilities and , and - in it, for example, there are much more controlled devices than previous programs (iPod media players, Creative Zen, mobile phones, digital cameras, tape and Zip archiving tools, webcams, scanners).
The program provides three typical settings for access rights - for servers, workstations and laptops. In addition to device blocking, the program has the possibility access blocking files depending on their type. For example, you can allow read access to document files, but deny access to executable files. It is also possible to block access to devices not only by their type, but also by the physical port to which external devices are connected. One more setting access rights conducted by unique device identifiers.
The application administrator can maintain two types of device lists - those that are allowed by default ("white list") and those that are denied access ("black list"). An IT specialist can give temporary permissions to access devices or groups of devices on a single computer (implemented by generating a special code that can be transmitted to the user even if his computer is disconnected from the network and the application agent is unable to connect to the server ).
The program implements support for a new encryption function used in Windows system 7 called BitLocker To Go. This feature is used to protect and encrypt data on removable devices. GFI EndPointSecurity can recognize these devices and provide access to the files stored on them depending on their types.
Provides the administrator with a powerful reporting system. The statistics subsystem (GFI EndPointSecurity ReportPack) shows (in textual and graphical form) a daily summary of device usage both for selected computers and for all computers in general. You can also get statistical data on user activity by day, week, month, broken down by applications, devices, file access paths.
 One of the most common programs for protecting information from insiders in Russia today. is published in Russia under the brand name "1C: Distribution"
One of the most common programs for protecting information from insiders in Russia today. is published in Russia under the brand name "1C: Distribution"
The program provides control not only devices running Windows Mobile, but also devices running operating systems iPhone OS and Palm OS. At the same time, shadow copying of all overwritten files and data is also provided, regardless of which port these devices are connected to the monitored network. Shadow copying can be configured not only by device, but also by file type, and the type will be determined not on the basis of extensions, but on the basis of their content.
You can set read-only access for removable media, including tape drives. As an additional option - protection of media from accidental or deliberate formatting. You can also keep a record of all user actions with both devices and files (not only copying or reading, but also deleting, renaming, and so on).
Streaming compression can be used to reduce network load when transferring data received from agents and shadow copy files. Shadow copy data in large networks can be stored on multiple servers. The program automatically selects the optimal server, taking into account network bandwidth and server load.
Many organizations use disks protected by special encryption programs - ViPNet SafeDisk, PGP Whole Disk Encryption, DriveCrypt and TrueCrypt to protect data. For such disks, the program can set special "encryption policies", which allows you to allow only encrypted data to be written to removable devices. Work is also supported with Lexar JumpDrive SAFE S3000 and Lexar SAFE PSD flash drives that support hardware data encryption. In the next version, work with the data encryption tool built into Windows 7 on removable media BitLocker To Go will also be supported.

Shadow copying is designed not only to save copies of files, but also to analyze the moved information. can perform full-text search on the contents of files, automatically recognizing and indexing documents in various formats.
Already announced new version a program that, in addition to a full-fledged search, will also implement content filtering of files copied to removable storage devices of any type, as well as control of the content of data objects transmitted from a computer via network communication channels, including email applications, interactive web services, social media, forums and conferences, the most popular instant messaging services (Instant Messengers), file exchanges via FTP, and Telnet sessions
Unique in the new version is the technology of text data filtering in the network and local document printing channel for jobs in PCL and PostScript formats, which allows blocking or allowing printing of documents depending on their information content.
conclusions
|
Remote control clients | ||||
|
Control via MMC snap-in | ||||
|
Centralized policy setting, control and recovery | ||||
|
Control of external devices |
USB only | |||
|
WiFi adapter control | ||||
|
Palm OS device control. iPhone/iPod |
Limited |
Limited |
||
|
Support for whitelisting technology | ||||
|
Support for media whitelisting technology | ||||
|
Support for external encrypted drives | ||||
|
Blocking keyloggers | ||||
|
Limiting the amount of data copied | ||||
|
Controlling data by type | ||||
|
Centralized logging | ||||
|
Shadow Copy |
USB only |
USB only |
Partially | |
|
Shadow copying print data | ||||
|
Graphical logging and shadowing reports | ||||
|
Full text search in shadow copy data |
The first two of the programs discussed can be used to information protection from theft, but their possibilities are limited. They "close" standard external devices to varying degrees, but their capabilities are limited - both in terms of settings and in terms of analyzing user work. These programs can be recommended "for testing", to understand the very process of protection. For large organizations that use a variety of peripheral equipment and require analysis of user activity, the above programs will be clearly insufficient.
For them, it is better to pay attention to programs - and. These are professional solutions that can be used in companies with both small and large number of computers. Both programs provide control of various peripheral devices and ports, have powerful analysis and reporting systems. But there are significant differences between them, so the company's program GFI in this case can be taken as the base. can control not only devices and work with data, but also the use software. This feature "pulls" it from the "Device Control" niche to the "Content-Aware Endpoint DLP" segment. New, announced capabilities allow it to sharply break away from its competitors due to the emergence of the ability to analyze content at the time the user performs various actions with data, including streaming, as well as by controlling a number of network communication context parameters, including email addresses, IP addresses, user identifiers and network application resources, etc. it is possible at partners "1Soft".
Mikhail Abramzon
All rights reserved. For information about using this article, please contact site administrators